thoughts on style, the TLS, and errors
The disclosure of the recent GnuTLS vulnerability forces me, as if against my will, to retread some tired ground. It’s been a busy week. For serious this time.
more...
The disclosure of the recent GnuTLS vulnerability forces me, as if against my will, to retread some tired ground. It’s been a busy week. For serious this time.
more...
I’m reading a CloudFlare blog post about serialization in Lua, and I’m thinking this might be useful. Then I scroll down to see what it looks like in action.
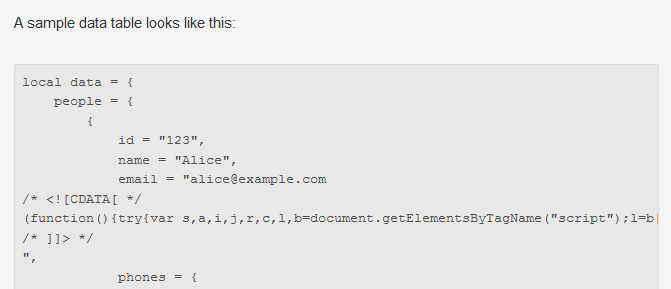
Err, that looks kinda weird. Now I’m thinking maybe this isn’t the serialization library for me.
Perhaps it’s just a mistake? View source.
<p>A sample data table looks like this:</p>
<pre><code>local data = {
people = {
{
id = "123",
name = "Alice",
email = "<a class="__cf_email__" href="http://www.cloudflare.com/email-protection" data-cfemail="f3929f9a9096b3968b929e839f96dd909c9e">[email protected]</a><script type="text/javascript">
/* <![CDATA[ */
(function(){try{var s,a,i,j,r,c,l,b=document.getElementsByTagName("script");l=b[b.length-1].previousSibling;a=l.getAttribute('data-cfemail');if(a){s='';r=parseInt(a.substr(0,2),16);for(j=2;a.length-j;j+=2){c=parseInt(a.substr(j,2),16)^r;s+=String.fromCharCode(c);}s=document.createTextNode(s);l.parentNode.replaceChild(s,l);}}catch(e){}})();
/* ]]> */
</script>",
phones = {Ah, yes. The email protector has protected dear Alice’s email, but didn’t quite manage to get out of its own way. I’m assuming nobody typed that mess in on purpose, which means CloudFlare has some automatic protection injecting proxy magic. Too much magic for me.
More WAF magic: https://scalewithlee.substack.com/p/when-etchsts-breaks-your-substack
Apple recently made a booboo, unlike any other booboo in the history of programming. Even though Apple’s bug is unprecedented, here’s a brief overview of some predecessor bugs.
more...
signify was (is) developed on OpenBSD-current and depends on a few features only found there. The first signed OpenBSD release, 5.5, will also be the first release to include signify. What to do if you’re running OpenBSD 5.3 or 5.4 and want to verify the 5.5 release you just downloaded is legit? You need the signify backport.
It’s all the necessary files packed into one directory. It should work on a few previous OpenBSD releases, and possibly other BSD systems, but beyond that it’s a lost cause. I don’t have much interest in making a true portable version.
This tgz also includes the set of public keys for 5.5 and 5.6. Building is simple. Run make and make install.
Several years ago, when Heroku was young and fresh, I had a question about their service. The only way to ask them a question was to create an account and file a support ticket, so that’s what I did. Some time passed and then suddenly I started receiving monthly Heroku newsletters. While I don’t recall there even being such a checkbox when I signed up, I am always fastidious about not opting in to receive such junk, even with fiendish “By not unchecking this box, you agree to not unsubscribe from our crap” phrasing, but nevertheless I find myself enrolled in their newsletter.
I have been ignoring the newsletter because unsubscribing is usually more trouble than it’s worth and my spam filter knows exactly where to put it. Eventually, somebody (or something) at Heroku caught on and a month ago I received this email:
“You are receiving this email because we do not have a current subscriber status on you for Heroku emails.“
You’d think no status would imply no newsletter, right? That email was followed an hour later by the January newsletter. The status email itself continued,
“If you would rather not opt-in to receive Heroku emails, you do not need to take any action. We will automatically change your status to opted-out within the next 30 days.“
Today I received the February newsletter.
Today I received the March newsletter. Looks like Heroku has decided to change my status to opt-in instead. Thanks.
Despite my reservations about two factor auth, I decided to try implementing it. Don’t knock it til you’ve done it, right? I’ve previously played with Duo Security’s login_duo, and they have a nicely polished mobile app, but the command line tool doesn’t quite feel integrated with the rest of the system (it’s user opt-in, not admin mandated). Plus, it’s more fun to build your own. For this experiment, I picked Pushover as factor number two, which also comes with a nice app which can be used for other things as well. Now we just need some code to talk to Pushover.
more...
A more difficult challenge than Inbox Zero, but after years of effort I’ve finally achieved it. Facebook Zero. I now know everything my friends have ever done. There is nothing left to read about.
Despite their wonky customer service, I have generally been happy with Comcast’s technical service. Occasionally though, I have to question what in the world is going on with their network. Recently I noticed that my internet connection would alternate between working and not on roughly a two minute interval. One minute things work fine, the next minute nothing works at all, the next minute everything is fine. During the blackout minutes, making a new connection would timeout, but established ssh connections would remain up, but nothing would happen until the blackout was over. Here are a few pings I sent out (2014-02-13).
more...
The February 17th 2014 issue of Time magazine, with the Infinity Machine on the cover.
more...
I was reviewing the flak logs the other day (chasing an unrelated issue) when I noticed lots of requests with additional parameters, like utm_campaign=twitter. Huh? I’m not running any campaigns. GTFO.
I find these tracker tags in URLs annoying when other sites do it. It’s not the tracking that bothers me, but the fact that the URLs end up being long and ugly, and it means there’s several URLs for the same content. I much prefer canonical URLS. Different tracking URLs break duplicate detection on various link sharing sites, and trick the browser’s history feature. Boo.
Of course, it’s your site, you do what you want, but this is my site, so don’t dick with my URLs. To that end, flak now filters out extraneous parameters by driving you through a bounce screen. Hopefully this prevents the further sharing and posting of the infected URLs.